An agreement between two parties that is executed without a third party is referred to as a smart contract. This smart contract has a unique ability to transfer ether from end users to other contracts. A common smart contract architecture is Ethereum, which consists of computer programs that represent smart contracts.
This article aims to provide an introduction to smart contracts and a detailed guide to understanding smart contract security to improve it. Our discussion will begin with what is a smart contract, move on to its security, discuss the need for it, and conclude with some thoughts for the future.
How does a blockchain work with Smart Contracts? A brief explanation of smart contract security
Smart contracts in blockchain technology serve to store data and run when predetermined conditions are matched. With the implementation of the smart contract agreement, the participants are allowed to determine their results immediately without any further delay. This improves the trust between the two parties by neglecting third-party involvement.
In other words, the smart contract works automatically and triggers the next action only when the conditions are met. This performance can result in the form of money exchange, delivery services, and unlocking of confidential data by digital rights management. In this way, privacy information can be tailored to suit the specific request, strengthening privacy protection.
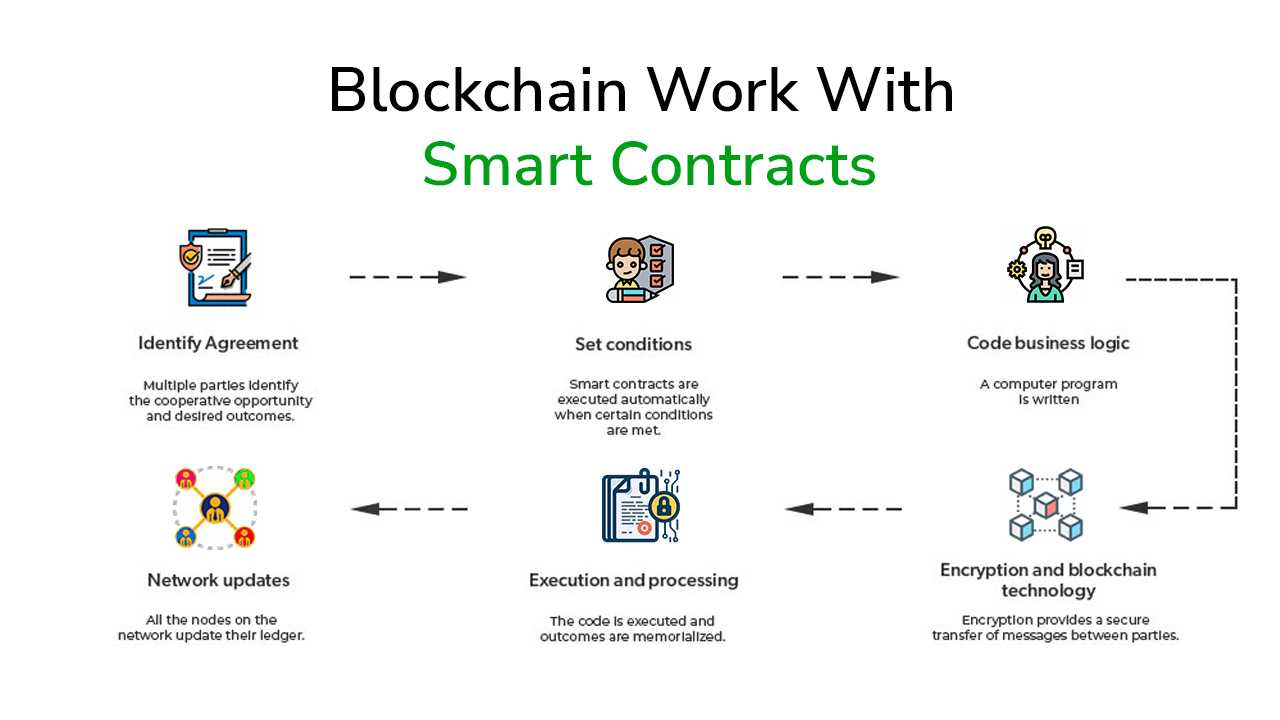
Most smart contracts are developed and distributed to manage the diversity of the structure. There are many different ways to implement it, such as using it for blockchain or ledger technology or combining it with several payment methods. This function processes a number of multiple tasks, transactions, or processes in accordance with programmed parameters.
To build trust and enable secure transitions between the users, smart contract security should be developed with the right security principles.
What is smart contract security?
During the process of implementing the smart contract blockchain, security plays a critical role. Smart contract security refers to the principles and practices used by developers and exchanges to ensure that they are protected from risk. The blockchain is the major game changer for cryptocurrencies, and it is therefore vulnerable to many flaws and vulnerabilities.
This vulnerability commonly happens when there is no proper smart contract audit. For the smart contract example, in the past few years, millions of dollars have been frequently drained from the smart contract wallet. Because of these reasons, it is crucial to prepare your smart contracts before deployment with effective techniques and preventative methods.
The development phase of a smart contract provides plenty of opportunities for fixing bugs, which is why developers need to be informed about contract security. However, users should understand security since smart contracts will interact with their wallets.
Vulnerabilities in Smart Contracts: An Overview
Smart contracts are agreements between parties, executed through a digital medium. While they have many advantages over conventional methods of contract enforcement such as facilitating automated actions with guaranteed results and eliminating human error, they also present new risks.
For example, they do not allow for human intervention if something goes wrong, and such defects are often impossible to rectify. The potential for vulnerabilities in smart contracts could be a security hazard and a target for malicious cybercriminals. In some cases, financial losses can result from a system's collapse even if there are no external exploiters.
In the following secession, we will discuss the 6 most common vulnerabilities to consider when deploying a smart contract on a blockchain.
Reentrancy Attacks - In smart contract reentrancy attack is considered one of the destructive strategy attacks. Which leads to complete damage to the contract or hacking the important information from the data. Common reentrancy occurs in smart contracts when the function calls another contact through an outer call. This results in an unwanted loop and keeps repeating several times.
Low-Build Application Bugs - If the smart contract was not developed as per the security principles, then there are chances for acquiring error issues. Application bug exploitation is most commonly seen in smart contracts that are developed poorly. When a decentralized platform gets programming flaws, the attacks can directly impact the smart contract wallet. That might lead to the loss of funds in the wallet.
Malicious Users - Because of the popularity of the smart contract in the blockchain, most of the malware takes place on the internet. Many spammers send malicious mail to some of the users or use the original user’s identity to commit fraud. These are some of the harmful behaviors that took place in the smart contract. Another way the malware attacks are made through requesting the users to connect their wallet through bogus websites for getting perks.
Unexpected Flaws in the Protocols - In recent years, blockchains are facing exploits based on poor consensus. These flaws in the consensus protocols will cost higher based on the attacks. If your protocols are weak then there are chances to get 51 percent attack and 34 percent assault.
Unexpected Logic Flows - When the integer variable is fixed size data then over/underflows occur. If the integer variable is able to store the data numbers between 0 to 250. As a result, the values that are above or below the fixed values there will have the chances to over/underflow. These vulnerabilities might create unexpected logic flows in the smart contract.
Wrong Calculations - Smart contracts are designed to deal with a large amount of money and various types of tokens. Handling improper mathematical calculations and fee calculations can result in loss of funds and a high probability of getting locked.
These are some of the 6 most common vulnerabilities to consider when deploying a smart contract on a blockchain. These smart contract vulnerabilities can be overcome with proper development. In CryptoApe, we follow the security principles to build the best smart contracts for blockchain users and entrepreneurs.
The Step-by-Step Process: How Does CryptoApe Enhance Smart Contract Security?
The first thing everyone should understand is that smart contract security is based on a set of coding principles. The contract should be developed according to those set of principles to overcome the smart contract vulnerabilities in the blockchain. We at CryptoApe have an experienced team of blockchain software/app developers.

They build smart contract security flawlessly to get rid of malicious users and enhance the contract wallet. Here are some of the practices that we follow while developing and before deploying the smart contract as follows:
Smart Contract Security Auditing and Testing - During developing the blockchain software, we aren’t able to see every bug and that's why it is critical to run preliminary tests. To make the testing the best, we use all the testing tools to check the bugs and recover it before deploying it. Alike testing security auditing is one of the necessary steps for ensuring smart contract security.
Maximum Features Usage - We use to upgrade the smart contract with additional key features, this is the best practice to manage the amount of risk. This could easily help the developers to inspect the error that occurs in the code and a similar development process will be used to overcome it before handing it over to the client.
Security Monitor/Alert Tool - In blockchain technology the blacklisted hackers and oddenders are real. To get rid of it, we deploy tools to help us to get notified in case a hacker is tempering with the client’s smart contract.
These are some of the procedures that we use at CryptoApe to create the best smart contract in accordance with the needs of the business owner. Because smart contracts are the foundation of blockchain technology, effectively developing it will increase utilization and improve user experience. It is the ideal time to choose one of these solutions given the fast scalability of the blockchain smart contract deployment.
Our developers want to reduce errors and boost security by making contracts as quick and easy to use as feasible. The creation of an enhanced live smart contract can increase complexity and inaccuracy. We advise choosing a straightforward smart contract deployment and afterwards upgrading the features in line with market needs.
Final Words
Today, any sector that makes use of blockchain technology has access to smart contracts. Our smart contract has great security because it deals with assets of higher value. which sought to protect your data from the security flaws in smart contracts. Finding the top smart contract developers on the market may seem like a financial hardship.
No need to worry; the CryptoApe project developers will take more factors into account while creating smart contract security. We use the third-party smart contract audit tool as part of our standard operating procedure to increase the security of the smart contract. We offer genuine returns on your investment along with the necessary smart contract security. You may be confident that you will be more lucrative and competitive as a result.



